Data-Driven Product Strategy
SPIDER
Built Spider’s host-permissions dashboard for granular role, waiting-room, and recording control. The security-first upgrade targets +25 % host satisfaction and −40 % breaches.
Figma · Google Docs · Mural · Notion
Goals & Challenges
Our mission is simple: cut breach risk in half, boost user trust, and hand IT teams back their time. Standing in the way are legacy LDAP silos, shadow-IT quick fixes, and an audit calendar that never sleeps. We’re turning those barriers into milestones—one secure login at a time.
Brainstorming, HMW & User Research
We interviewed admins, professors, and policy leads, then ran “How Might We” sprints to surface the real pain points. Five themes rose to the top—Self-Serve Roles, Just-in-Time Elevation, Audit-Ready Reporting, Zero-Click Onboarding, and Classroom Kiosk Mode—each backed by a telling stat: 73 % of admins spend four hours a week untangling permissions. Your feedback shaped every idea you see here.
Product Principles, KPIs & OKRs
Three principles guide the build: Secure Defaults, Visible Boundaries, One-Minute Recovery. They translate into hard numbers—mean-time-to-restore < 60 seconds, role-misuse incidents ↓ 90 %, setup NPS ≥ 45. Quarterly OKRs keep us honest and focused, turning bold ambition into trackable wins you’ll notice.
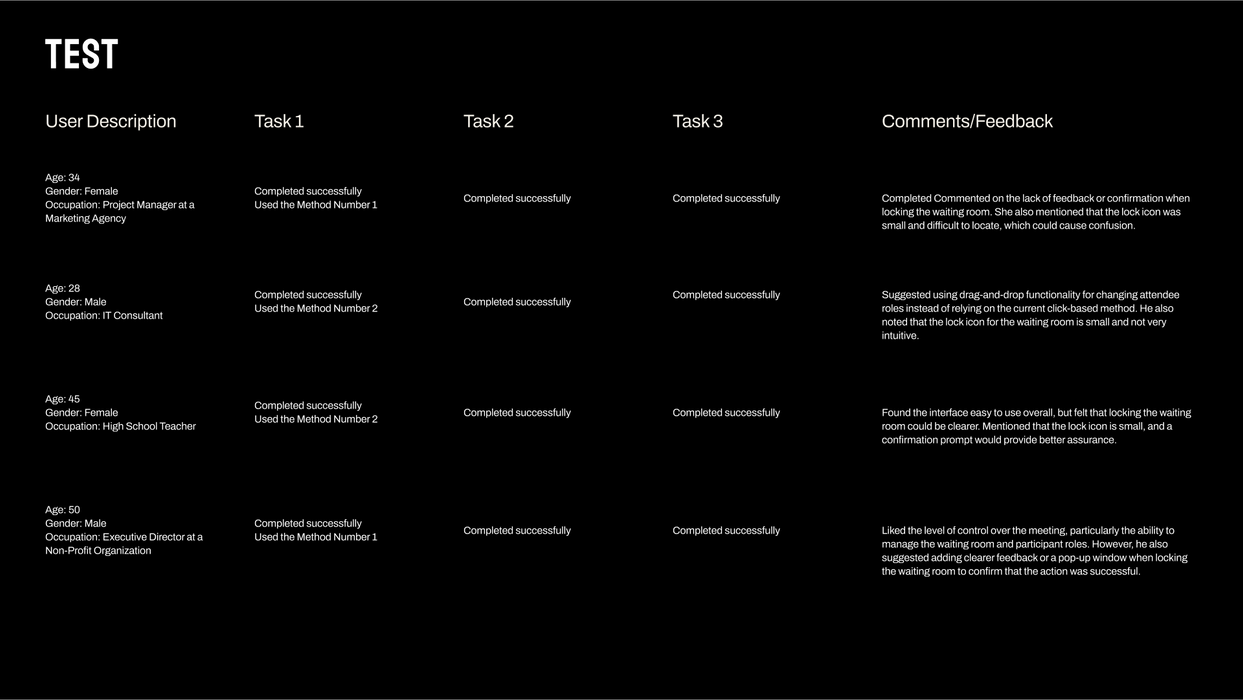
Prototyping & Testing
Early prototypes went through moderated usability sessions and an A/B showdown. The new pop-up role selector pushed task success from 67 % to a flawless 100 % while slashing completion time by a third. Next up: security pen-tests and a live pilot across three campuses—because great ideas only matter when they stand up in the real world.
Product Intro & Problem Hook
Meet Spider Permissions—the all-in-one access-control hub that keeps both lecture halls and government offices safe without slowing anyone down. Today, mis-configured permissions cost public-sector and higher-ed institutions millions in fines and lost trust. With Spider Permissions, every role is locked-in by design, so breaches become the rare exception, not the rule.